The Week - Ending 18 July 2025
Round-Up
-
CVE-2025-5777 update: Citrix has admitted to public exploitation - Citrix updated their blog after industry and CISA pressure, adding the exploit to the Known Exploited Vulnerabilities catalogue last week. Citrix has also provided further detail on how to threat hunt against CitrixBleed2 (Netscaler Blog).
Something to bring your attention to here by Security Researcher Kevin Beaumont - the patching notes are still missing a key point “if it’s a HA pair you need to additionally reset other session types or you’re still vulnerable to session hijack after patching” Mastodon . His updated scan data shows over 3,000 devices still unpatched (here).
UPDATE - Dutch Department of Justice internal services down- speculation is that this is related to Citrix Netscalers. They took down their internet services this morning (Friday 25/07/25) after the Dutch NCSC detected some in the ministry’s environment. As reported by the NRC: “The NCSC [National Cyber Security Center] received a signal that there is a potential vulnerability,” the spokesperson said. “A thorough analysis of the Public Prosecution Service’s environments has given reason to believe that this potential vulnerability has indeed been exploited.”
Its been reported that while the department did patch, due to incomplete patching instructions that more orgs may well be hit with similar problems even though they may believe they are patched. The Dutch NCSC are recommended that all orgs threat hunt against threat actors if they have Citrix Netscalers.
Techzine | NRC.NL | Dutch News | NCSC
-
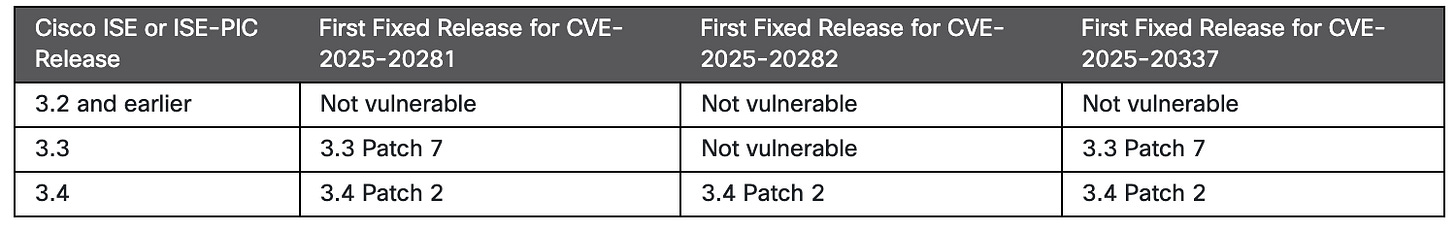
Max Severity Cisco Identity Services Engine bug CVE-2025-20337 - A critical 10.0 CVSS vulnerability allowing pre-auth attacks via a specially crafted API request. This relates to previously fixed bugs CVE-2025-20281 and CVE-2025-20282, both also rated 10.0, so unfortunately its time to patch again. Patch 7 has only recently become available. Cisco Response | Bleeping Computer
-
Threat Actor targets SonicalWall devices with Malware and Rootkits - SonicWall EOL devices are being targeted by UNC6148 says Googles Threat Intelligence Group (GTIG). The deployed malware named OVERSTEP, acts as a backdoor with some novel anti-forensic features capable of deleting evidence of intrusion. As is often the case, these targeted devices are EOL and should be replaced. Recommendation here is to examine logs, isolating impacted devices, and working with SonicWall to confirm the extent of malicious activity. Due to the anti-forensic nature of the malware, incident response may need to be invoked to investigate.
-
The Co-op Group have confirmed personal data of 6.5 million members has been stolen -Shirine Khoury-Haq, the CEO, confirmed to the BBC that members’ data was stolen. BBC News They confirmed that not all systems are up and running yet, but on the face of it I thought there general response has been pretty decent. (Apart from their initial silence around member data being stolen)
They have announced a partnership with The Hacking Games to pilot a programme designed to redirect young cyber talent away from crime. The Co-op’s 38 academies will participate in the pilot. Further details are available in their press release.
-
WING FTP Server under active exploitation - CVE-2025-47812 with a CVSS score of 10.0 could lead to unauthenticated remote code execution with all versions prior to 7.4.4 effected. This has been added to CISAs KEV catalog. CVE-2025-47812
-
Cloudflare restricting access to Internet Piracy Websites in the UK - A notable change is that Content Delivery providers have started facilitating copyright infringement notices. Cloudflare now displays “Error 451 – Unavailable for Legal Reasons.” While ISPs have long been forced to block access to these sites, it’s a first that Cloudflare is now also following suit. Cloudflare operates a public resolver (1.1.1.1), provides ZTNA services, and, of course, operates a large public CDN. They appear to be using geo-blocking to restrict access to these sites in the UK only.
Currently, the targeted sites are limited in number and don’t seem to include the much larger list that UK ISPs block. It’s worth noting that the blocks also appear to affect any sites that use Cloudflare for website caching.
OpenAI Release new Agentic AI Agents
OpenAI yesterday (17/07/25) released its ChatGPT Agent as part of its agentic strategy. It brings together ChatGPT’s Deep Research, an Operator that can interact with websites, and the general GPT model into a unified system allowing it to carry out tasks on its own virtual computer.
They’ve given the agent with a visual browser allowing it to interact with websites, a text-based browser, terminal, and direct API access. The agent can also use ChatGPT Connectors to connect to apps such as Gmail and GitHub.
In comparison to what Microsoft has managed so far with Copilot, this is very interesting—but whether it will actually bring real-world value is something I guess we’ll see. Some guardrails have already been put in place to restrict the agent’s ability to interact with financial-related tasks.
Availability
Directly from OpenAI:
"ChatGPT agent starts rolling out today to Pro, Plus, and Team; Pro will get access by the end of day, while Plus and Team users will get access over the next few days. Enterprise and Education users will get access in the coming weeks. Pro users have 400 messages per month, while other paid users get 40 messages monthly, with additional usage available via flexible credit-based options.
We are still working on enabling access for the European Economic Area and Switzerland."Cloudflare Outage 14/07/2025
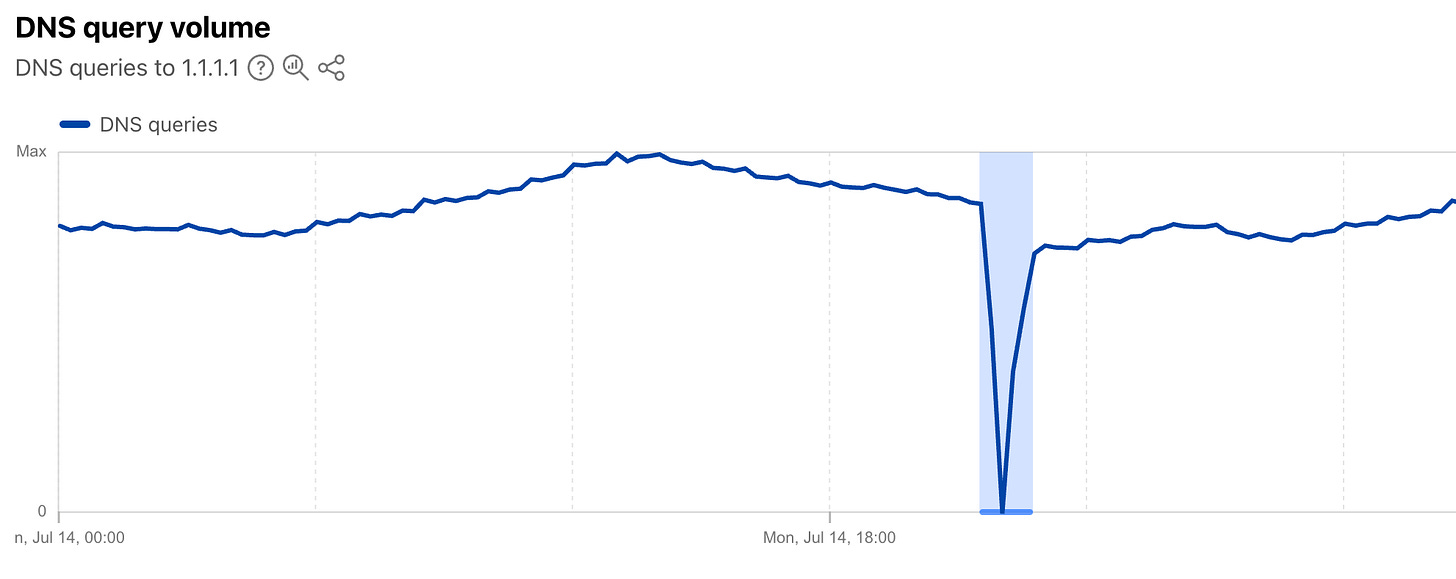
Cloudflare have admitted to a borked configuration change that caused an outage to the 1.1.1.1 resolver which effected the majority of the 1.1.1.1 users globally., being a DNS resolver meant this caused a fair amount of issues for users accessing services on the web.
Initially, it appeared to be a BGP hack, but it looks like the configuration error withdrew the 1.1.1.0/24 route completely. Cloudflare (AS13335) withdrew 1.1.1.0/24 and 1.0.0.0/24. I assume Tata (AS4755) had always been announcing 1.1.1.0/24, and when Cloudflare withdrew the route, Tata’s announcement became active.
Cloudflare Blog Post Cloudflare Radar
Normally I would bring out my favorite DNS meme, but as always its always DNS until it isn’t and its actually BGP.
Call to Action
-
Patch your Cisco ISE environments ASAP
-
Review the updated scan data for CitrixBleed2 by Kevin
-
Replace your EOL Sonicwall devices
-
Upgrade WING FTP Server to version 7.4.4 or later.
That’s it for this week. Stay alert, patch fast, and I’ll catch you next week. Any feedback, feel free to reply or comment.
Extra Sources
Additional Sources I have used to pull together the above.
Cisco advisory on CVE-2024-20357: sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ise-unauth-rce-ZAd2GnJ6
NVD entry for CVE-2024-20357: nvd.nist.gov/vuln/detail/CVE-2024-20357
Bleeping Computer on Cisco ISE bug: bleepingcomputer.com/news/security/cisco-warns-of-new-actively-exploited-ise-rce-vulnerability/
Tenable/Cisco plugin details: tenable.com/plugins/nessus/195154
Google GTIG blog on SonicWall/OVERSTEP: cloud.google.com/blog/topics/threat-intelligence/sonicwall-secure-mobile-access-exploitation-overstep-backdoor
The Hacker News on UNC6148: thehackernews.com/2024/07/unc6148-backdoors-fully-patched.html
HelpNetSecurity deep dive: helpnetsecurity.com/2024/07/16/sonicwall-sma-devices-persistently-infected-with-stealthy-overstep-backdoor-rootkit/
Cybersecurity Dive on SonicWall: cybersecuritydive.com/news/threat-actor-targets-end-of-life-sonicwall-sma-100-appliances-in-ongoing-ca/721247/
The Guardian on Co-op breach: theguardian.com/business/2024/jul/16/co-op-boss-admits-all-6m-members-had-data-stolen-in-cyber-attack
The Times on Co-op and Hacking Games: thetimes.co.uk/article/co-op-partners-with-hacking-games-to-promote-ethical-careers-after-cyberattack-flgtcg69w
TechRadar on the Co-op breach: techradar.com/pro/security/data-of-all-6-5-million-coop-members-stolen-ceo-is-incredibly-sorry
CitrixBleed2 exploit warning: techradar.com/pro/security/citrixbleed-2-exploits-are-now-in-the-wild-so-patch-now
Akamai on CitrixBleed2 mitigation: akamai.com/blog/security/mitigating-citrixbleed-memory-vulnerability-with-appsec-engine
Horizon3.ai deep dive: horizon3.ai/attack-research/attack-blogs/cve-2024-5777-citrixbleed-2-technical-deep-dive
ReliaQuest threat spotlight: reliaquest.com/blog/threat-spotlight-citrix-bleed-2-vulnerability-in-netscaler-adc-gateway-devices/
Netscaler blog updates: netscaler.com/blog/news/netscaler-critical-security-updates-for-cve-2024-6543-and-cve-2024-5777
CISA Known Exploited Vulnerabilities (KEV) catalog: cisa.gov/known-exploited-vulnerabilities-catalog
Broadcom on CVE-2024-47812 (Wing FTP): broadcom.com/support/security-center/protection-bulletin/cve-2024-47812-wing-ftp-server-vulnerability-exploited-in-the-wild
NVD entry for Wing FTP RCE: nvd.nist.gov/vuln/detail/CVE-2024-47812
Huntress report on Wing FTP exploitation: huntress.com/blog/wing-ftp-server-remote-code-execution-cve-2024-47812-exploited-in-the-wild
Cybersecurity Dive on Wing FTP flaw: cybersecuritydive.com/news/hackers-exploiting-flaw-wing-ftp-server/720792/
Security Affairs on CISA adding Wing FTP KEV: securityaffairs.com/165681/hacking/u-s-cisa-adds-wing-ftp-server-flaw-to-its-known-exploited-vulnerabilities-catalog.html